Microsoft Sentinel (MDR)
Microsoft Sentinel (MDR)
Get a birds-eye view of the security landscape across your tenant, monitoring, responding to alerts, and neutralising threats.
Get the SIEM Plus XDR Workshop Brochure
CloudAssist is running a fully Microsoft-funded workshop on successful deployment and harnessing of Microsoft 365 Defender and Microsoft Sentinel security suite for enterprises.
The workshop is continually updated and recurring, but with limited spots available.
Complete the form below to assess your eligibility and get the Workshop Overview Brochure.

Microsoft Sentinel (MDR) Overview
Features
- Sentinel SIEM installation & implementation
- Outsourced maintenance and support of core Sentinel components
- Managed Security services, including monitoring, alerting, reporting and advice.
- Onboarding client log sources and configuration
- Machine Learning and AI support for bespoke, automated remediation needs
- Guided remediation, following alerts which identify significant vulnerabilities
- Guided incident response on containment and remediation
- Active threat hunting support (on request)
- Annual health check assessments of your SIEM implementation
Benefits
- Secure digital transformation and protect your cloud environment 24/7
- Focus on your core strengths – protecting your business
- Cut out the ‘noise’ and prioritise incident response
- Enable rapid detection, investigation, and response
- Save on internal recruitment and training
- Save on infrastructure and management overheads
- Protect against insider threat
- Maintain compliance with industry regulations
- Contact our experts today to find out more or request a free health check now.
Features
- Sentinel SIEM installation & implementation
- Outsourced maintenance and support of core Sentinel components
- Managed Security services, including monitoring, alerting, reporting and advice.
- Onboarding client log sources and configuration
- Machine Learning and AI support for bespoke, automated remediation needs
- Guided remediation, following alerts which identify significant vulnerabilities
- Guided incident response on containment and remediation
- Active threat hunting support (on request)
- Annual health check assessments of your SIEM implementation
Benefits
- Secure digital transformation and protect your cloud environment 24/7
- Focus on your core strengths – protecting your business
- Cut out the ‘noise’ and prioritise incident response
- Enable rapid detection, investigation, and response
- Save on internal recruitment and training
- Save on infrastructure and management overheads
- Protect against insider threat
- Maintain compliance with industry regulations
- Contact our experts today to find out more or request a free health check now.
Microsoft Sentinel Workshop
Defend Against Threats with SIEM Plus XDR
Get hands-on experience and learn to recognise and manage security threats across your tenant with this Microsoft-sponsored CloudAssist workshop.
XDR vs. SIEM vs. Incident Response

XDR
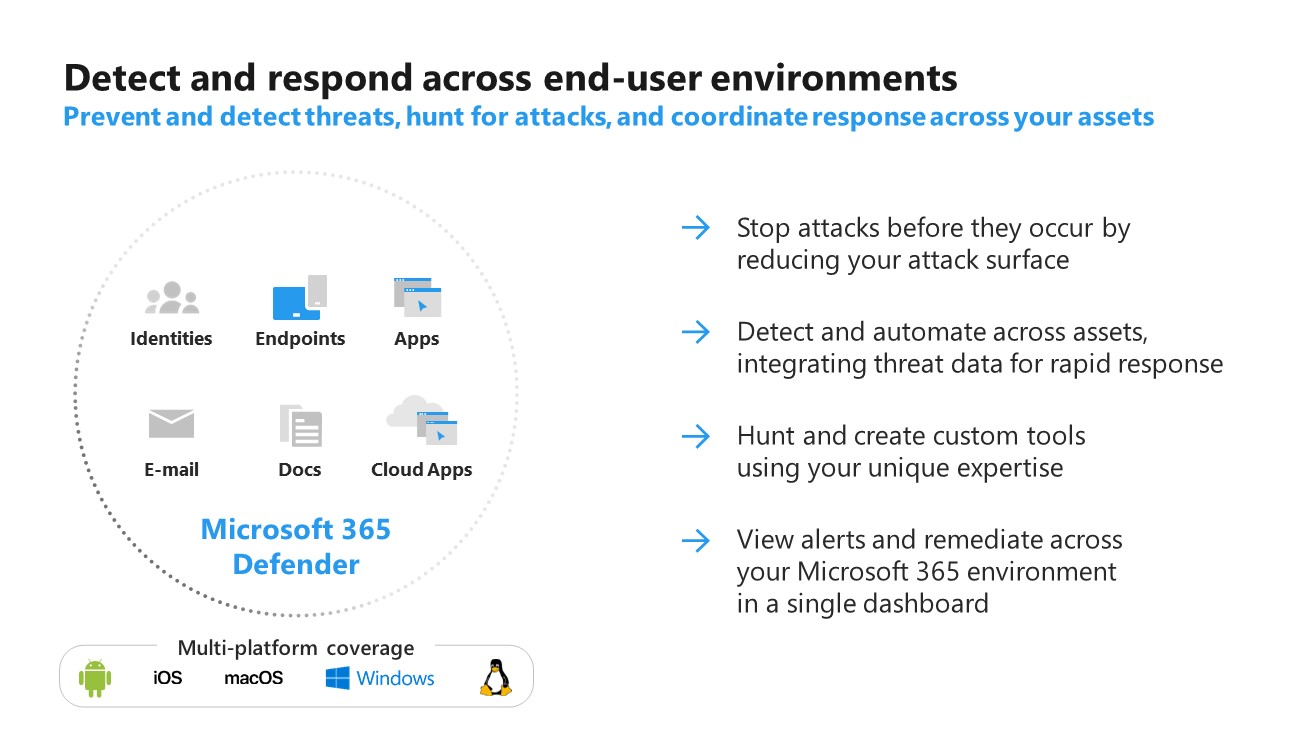
Extended detection and response, often abbreviated (XDR), is a SaaS tool that offers holistic, optimized security by integrating security products and data into simplified solutions. In contrast to systems like endpoint detection and response (EDR), XDR broadens the scope of security, integrating protection across a wider range of products, including an organization’s endpoints, servers, cloud applications, emails, and more. From there, XDR combines prevention, detection, investigation, and response, providing visibility, analytics, correlated incident alerts, and automated responses to improve data security and combat threats. Microsoft 365 Defender is an extended detection and response (XDR) solution that automatically collects, correlates, and analyses signal, threat, and alert data from across your Microsoft 365 environment, including endpoint, email, applications, and identities. It leverages artificial intelligence (AI) and automation to automatically stop attacks, and remediate affected assets.

SIEM
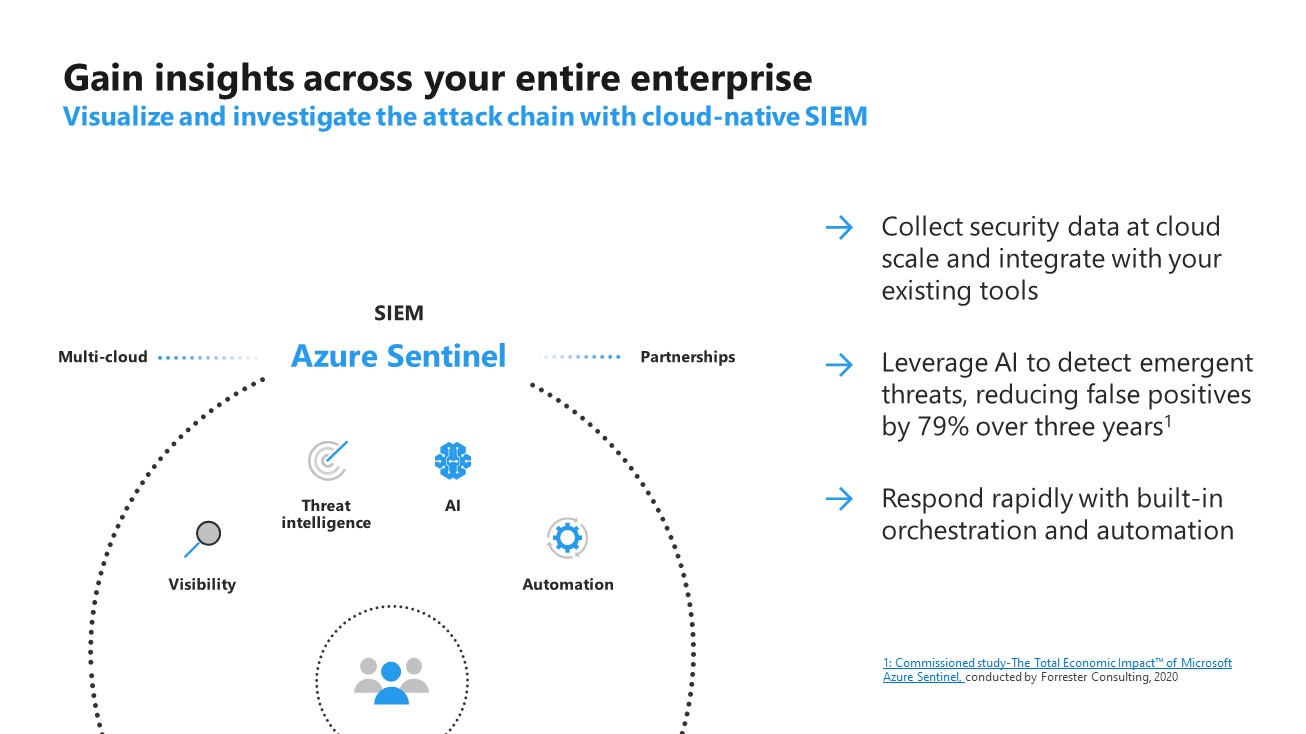
This is typically used to collect logs from all security devices with the exception of endpoints (though some may very well do that as well). This would include firewalls, IPS/IDS, network devices, Windows AD logs, various SaaS/Cloud apps (depending on the capabilities of the SIEM solution). In case of Azure Sentinel, Microsoft currently provides 60 types of data connectors and at Managed Sentinel we built an additional 65 that can bring data from virtually any type of log source. Some customers may choose just a managed SIEM service that is not considered an MDR as it only covers the maintenance of the SIEM platform and the development of tuning of detections, alerts and SOAR playbooks.

Incident Response
The Microsoft Security Services for Incident Response service will help you remove a bad actor from your environment, build resilience for future attacks, and mend your defences after a breach. Microsoft’s global team of experts leverages strategic partnerships with security organizations, governments around the world, and with internal Microsoft product groups to respond to incidents and help customers secure their most sensitive, critical environments. By leveraging comprehensive toolsets, Microsoft’s threat research, and signals from our security product stack, our experts will assist your organization in removing attackers, recovering environments, and reducing your attack surface.