Compliance
Compliance
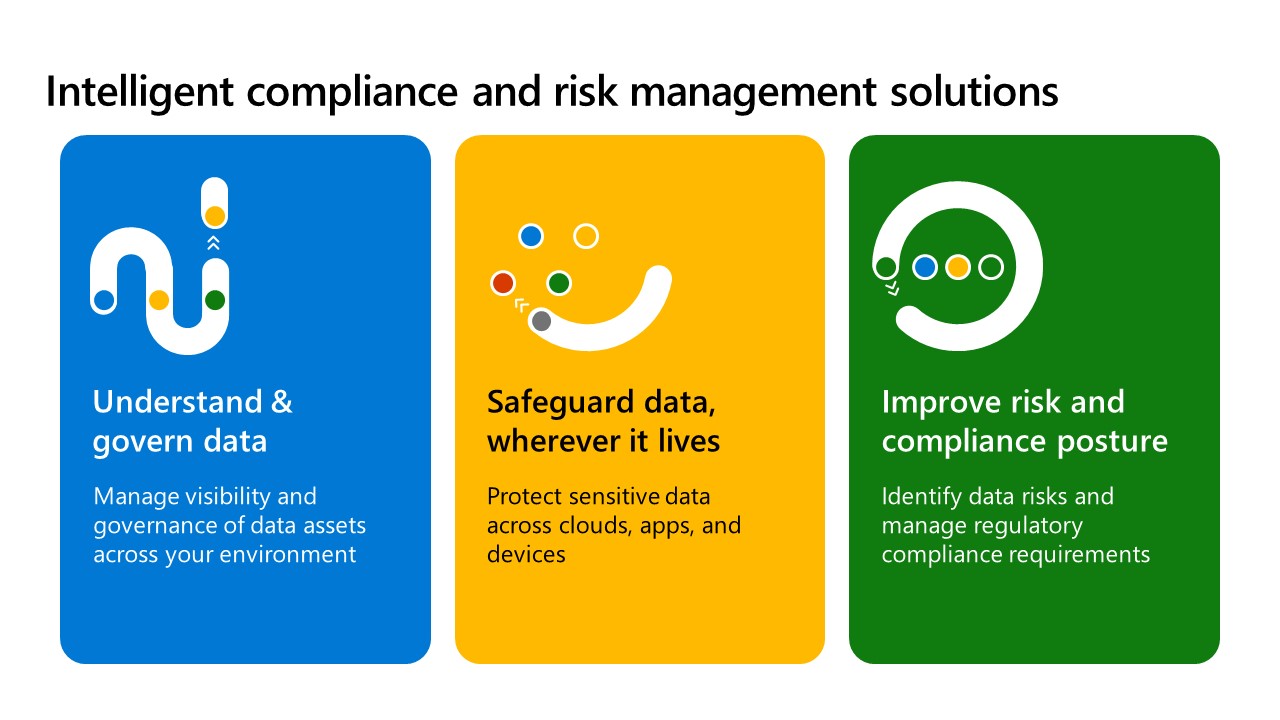
Microsoft Purview Compliance Manager provides Information Protection, Data Loss Prevention, Insider Risk Management, Auditing functionalities, and more.
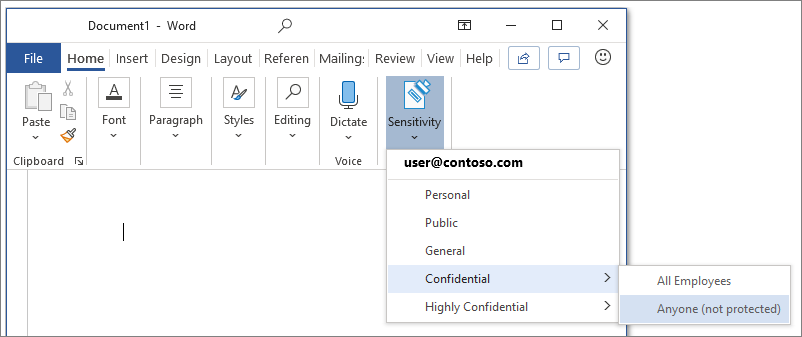
Configure sensitivity labels for your tenant so that your users can be recommended to start encrypting and protecting sensitive information.
Create and review your organization’s data loss prevention policies to prevent oversharing of sensitive information with external recipients.
- Configure insider risk management policies to help minimize internal risks and enable you to detect, investigate, and take action for risky activities.
*CloudAssist is offering fully Microsoft-funded workshops with FastTrack-ready support.
Configure sensitivity labels for your tenant so that your users can be recommended to start encrypting and protecting sensitive information.
Create and review your organization’s data loss prevention policies to prevent oversharing of sensitive information with external recipients.
- Configure insider risk management policies to help minimize internal risks and enable you to detect, investigate, and take action for risky activities.
*CloudAssist is offering fully Microsoft-funded workshops with FastTrack-ready support.
Microsoft Purview Compliance Overview



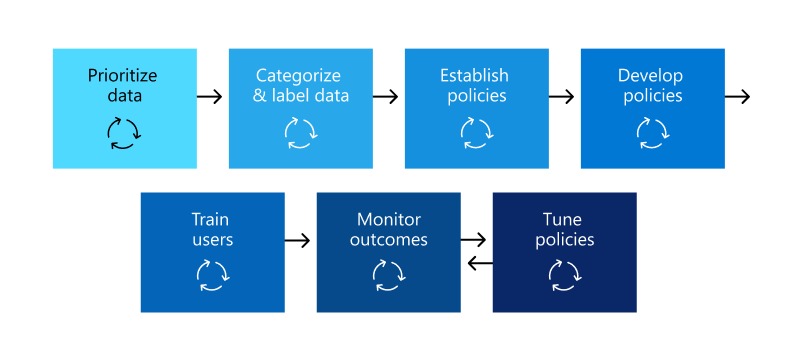
Your Data's Compliance Journey
Compliance Workshops with CloudAssist
Strengthen your organisation's compliance posture
Your organisation may be eligible for the following compliance workshops, fully sponsored by Microsoft and hosted by CloudAssist.
Complete the short form below to get immediate download access for two brochures that give an overview of the workshop contents.
Protect and Govern Sensitive Data


Mitigate Compliance and Privacy Risks

Check your enterprise's eligibility for this Microsoft-funded workshop:
Complete the short survey below on your interest in these Microsoft Compliance workshops, and we will assess your enterprise’s eligibility.
Please note that a minimum of 250 Microsoft-licensed end-user accounts is a basic requirement for Microsoft-funded eligibility.
Get Started
Configuration Analyzer for Microsoft Purview (CAMP)
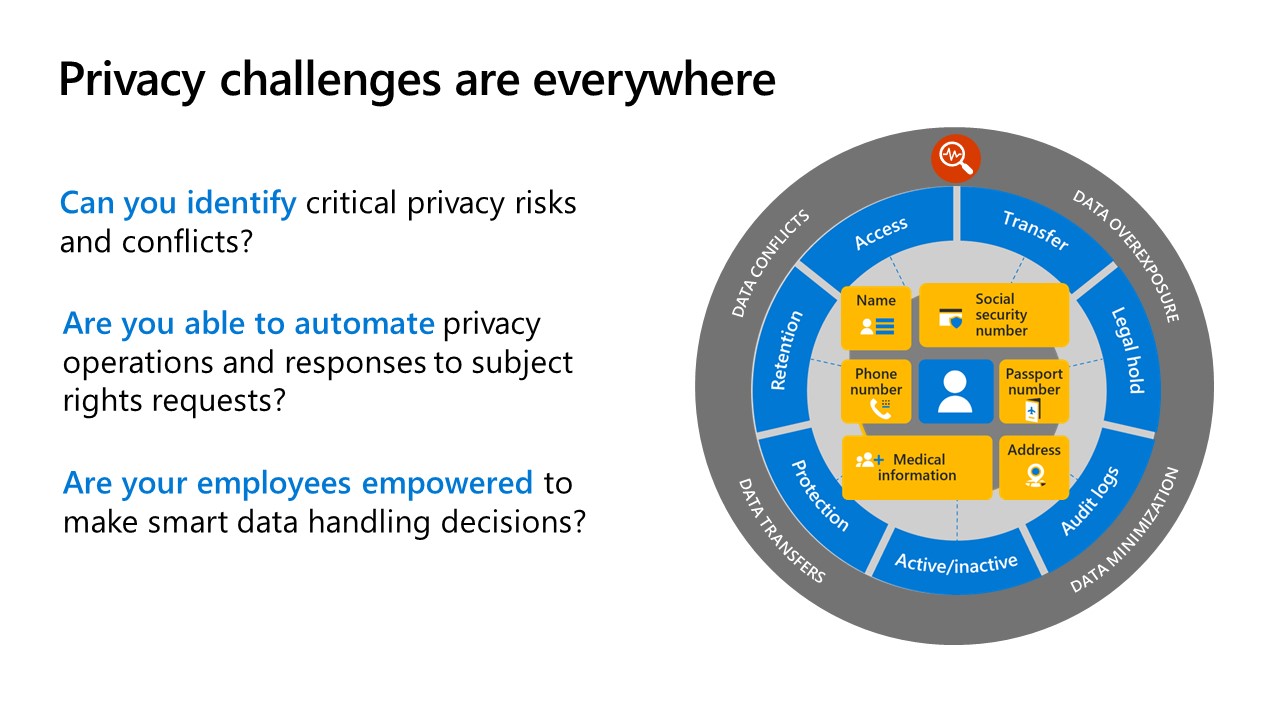
The Configuration Analyzer for Microsoft Purview (CAMP), formerly the ‘Microsoft Compliance Configuration Analyzer’ (MCCA), is a tool that can help you get started with Microsoft Purview Compliance Manager. CAMP is a PowerShell-based utility that will fetch your organization’s current configurations and validate them against Microsoft 365 recommended best practices. These best practices are based on a set of controls that include key regulations and standards for data protection and data governance.
CAMP can help you quickly see which improvement actions in Compliance Manager apply to your current Microsoft 365 environment. Each action identified by CAMP will give you recommendations for implementation, with direct links to Compliance Manager and the applicable solution to start taking corrective action.
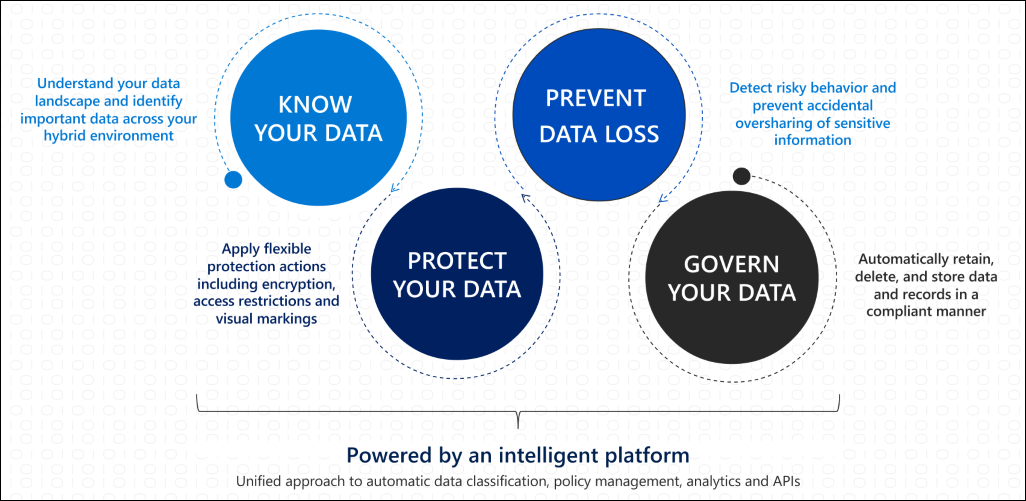
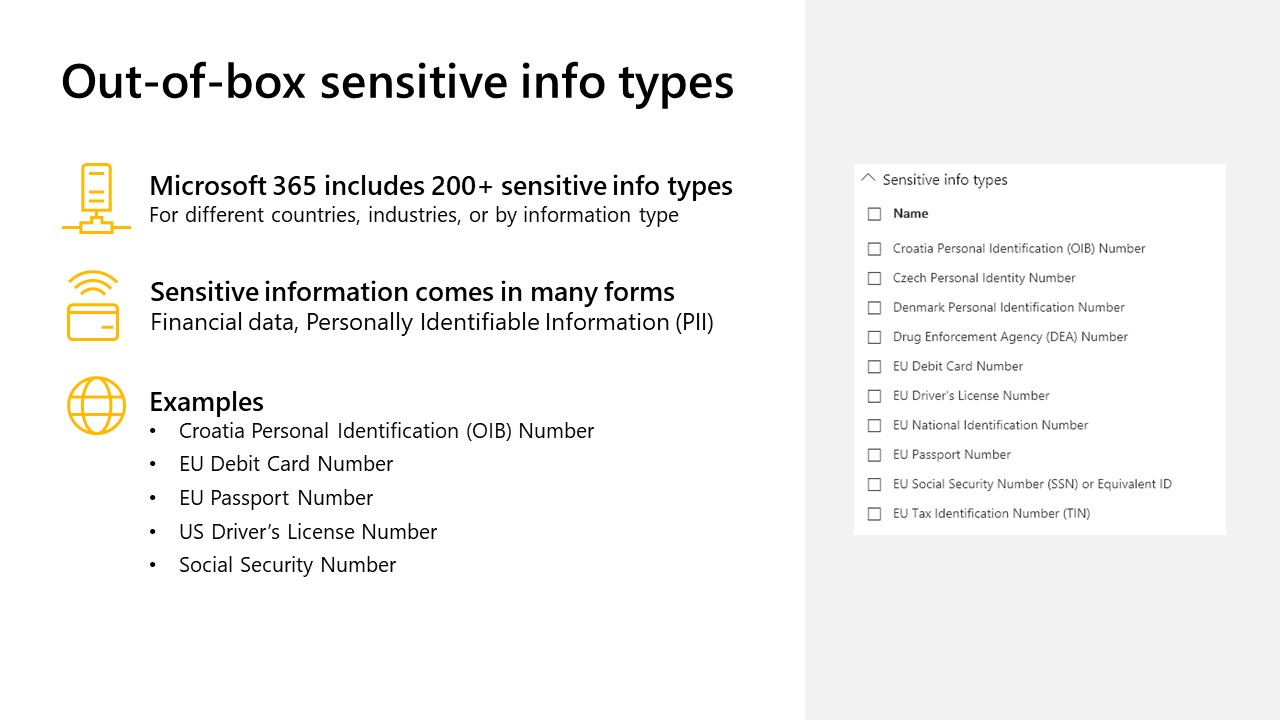
Microsoft Information Protection (MIP)
You can use sensitivity labels to:
-
Provide protection settings that include encryption and content markings. Content markings include headers and footers as well as watermarks, and encryption can also restrict what actions authorized people can take on the content.
-
Protect content in Office apps across different platforms and devices. Supported by Word, Excel, PowerPoint, and Outlook on the Office desktop apps and Office on the web. Supported on Windows, macOS, iOS, and Android.
-
Protect containers that include Teams, Microsoft 365 Groups, and SharePoint sites. For example, set privacy settings, external user access and external sharing, and access from unmanaged devices.
-
Extend sensitivity labels to Power BI: When you turn on this capability, you can apply and view labels in Power BI, and protect data when it’s saved outside the service.
-
Classify content without using any protection settings. You can also simply assign a label as a result of classifying the content. This provides users with a visual mapping of classification to your organization’s label names, and can use the labels to generate usage reports and see activity data for your sensitive content.
And much more…
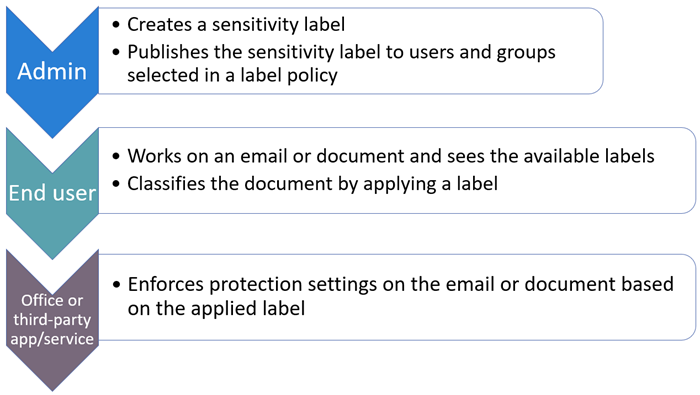
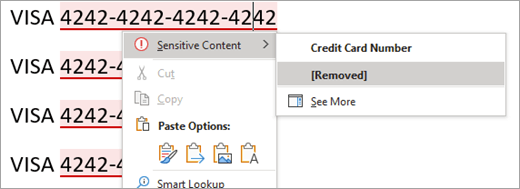
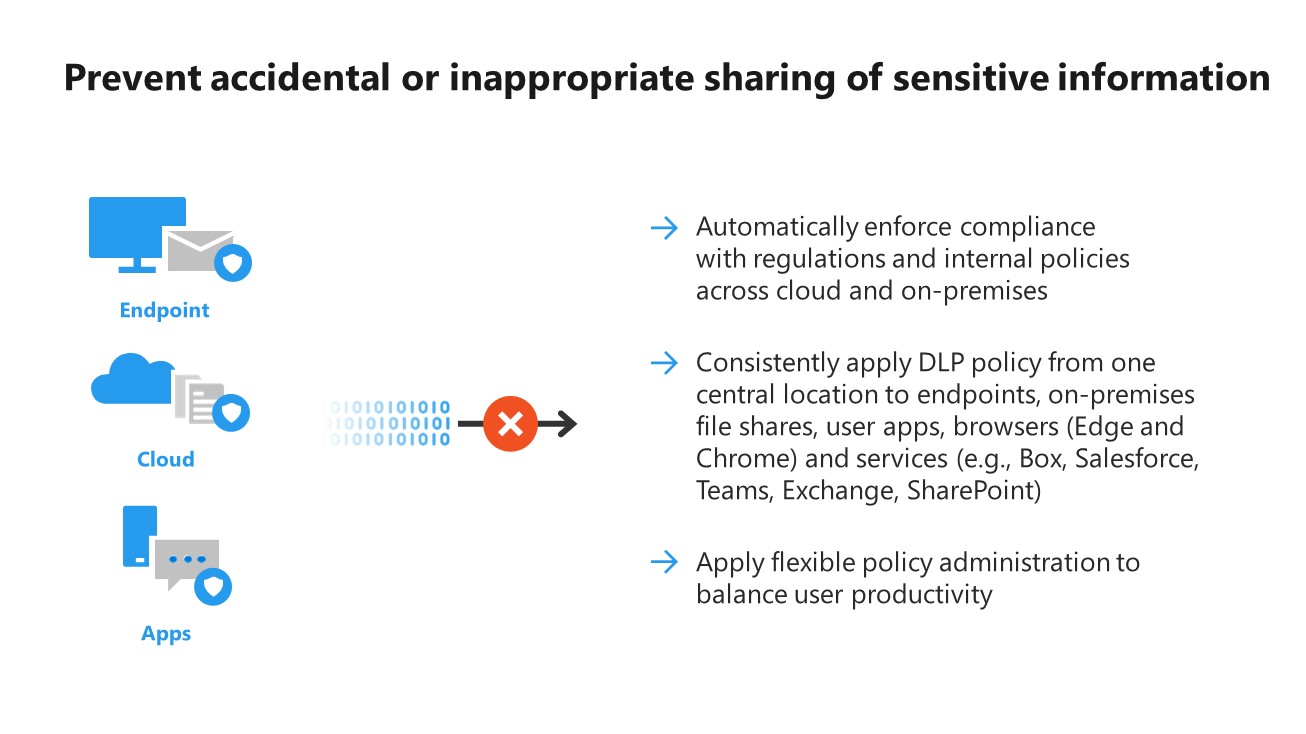
Data Loss Prevention
DLP policies are how you monitor the activities that users take on sensitive items at rest, sensitive items in transit, or sensitive items in use and take protective actions. For example, when a user attempts to take a prohibited action, like copying a sensitive item to an unapproved location or sharing medical information in an email or other conditions laid out in a policy, DLP can:
- show a pop-up policy tip to the user that warns them that they may be trying to share a sensitive item inappropriately
- block the sharing and, via a policy tip, allow the user to override the block and capture the users’ justification
- block the sharing without the override option
- for data at rest, sensitive items can be locked and moved to a secure quarantine location
- for Teams chat, the sensitive information will not be displayed
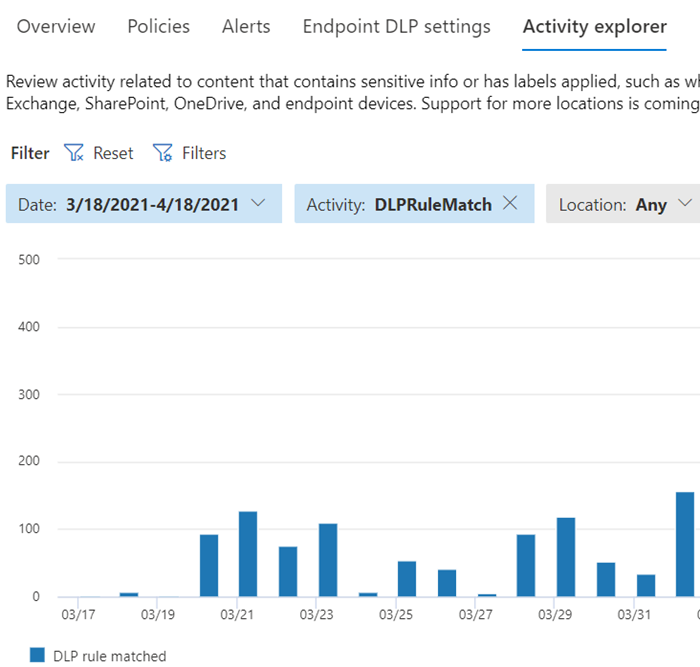
All DLP monitored activities are recorded to the Microsoft 365 Audit log by default and routed to Activity explorer. When a user performs an action that meets the criteria of a DLP policy, and you have alerts configured, DLP provides alerts in the DLP alert management dashboard.
Data Loss Prevention

DLP policies are how you monitor the activities that users take on sensitive items at rest, sensitive items in transit, or sensitive items in use and take protective actions. For example, when a user attempts to take a prohibited action, like copying a sensitive item to an unapproved location or sharing medical information in an email or other conditions laid out in a policy, DLP can:
- show a pop-up policy tip to the user that warns them that they may be trying to share a sensitive item inappropriately
- block the sharing and, via a policy tip, allow the user to override the block and capture the users’ justification
- block the sharing without the override option
- for data at rest, sensitive items can be locked and moved to a secure quarantine location
- for Teams chat, the sensitive information will not be displayed
All DLP monitored activities are recorded to the Microsoft 365 Audit log by default and routed to Activity explorer. When a user performs an action that meets the criteria of a DLP policy, and you have alerts configured, DLP provides alerts in the DLP alert management dashboard.




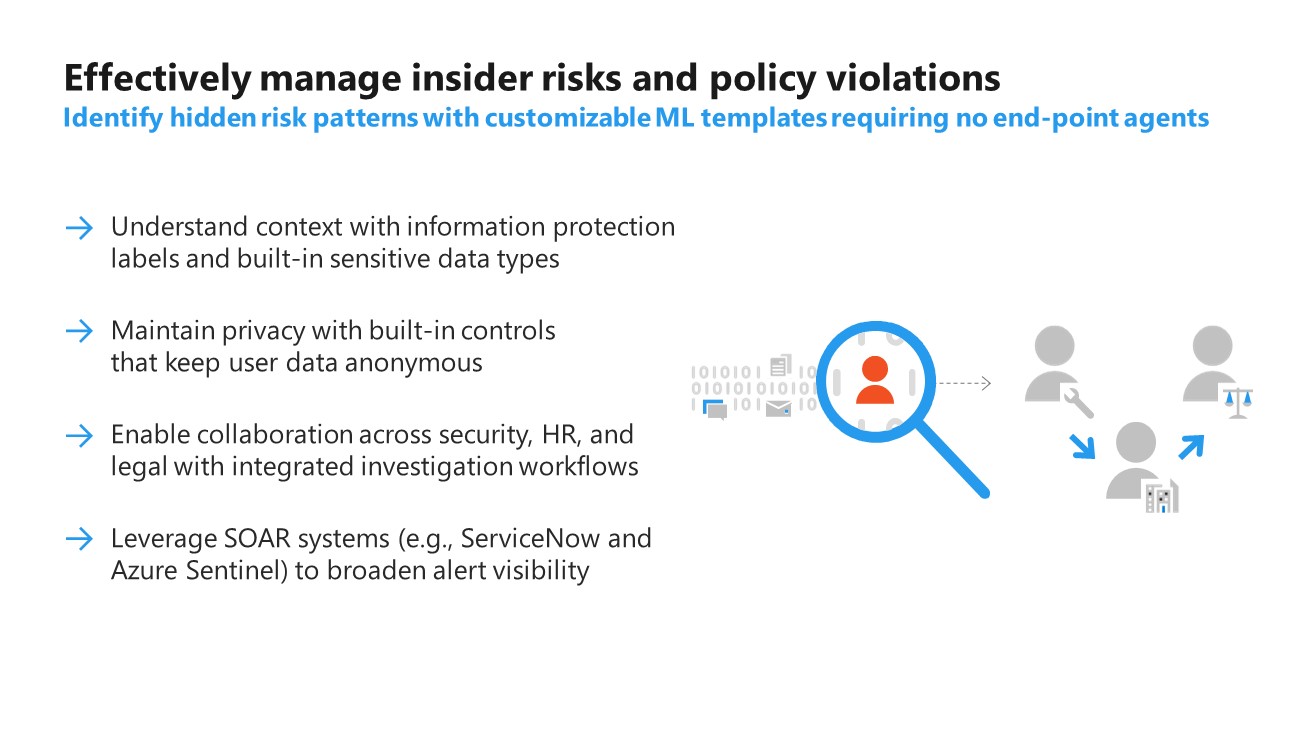
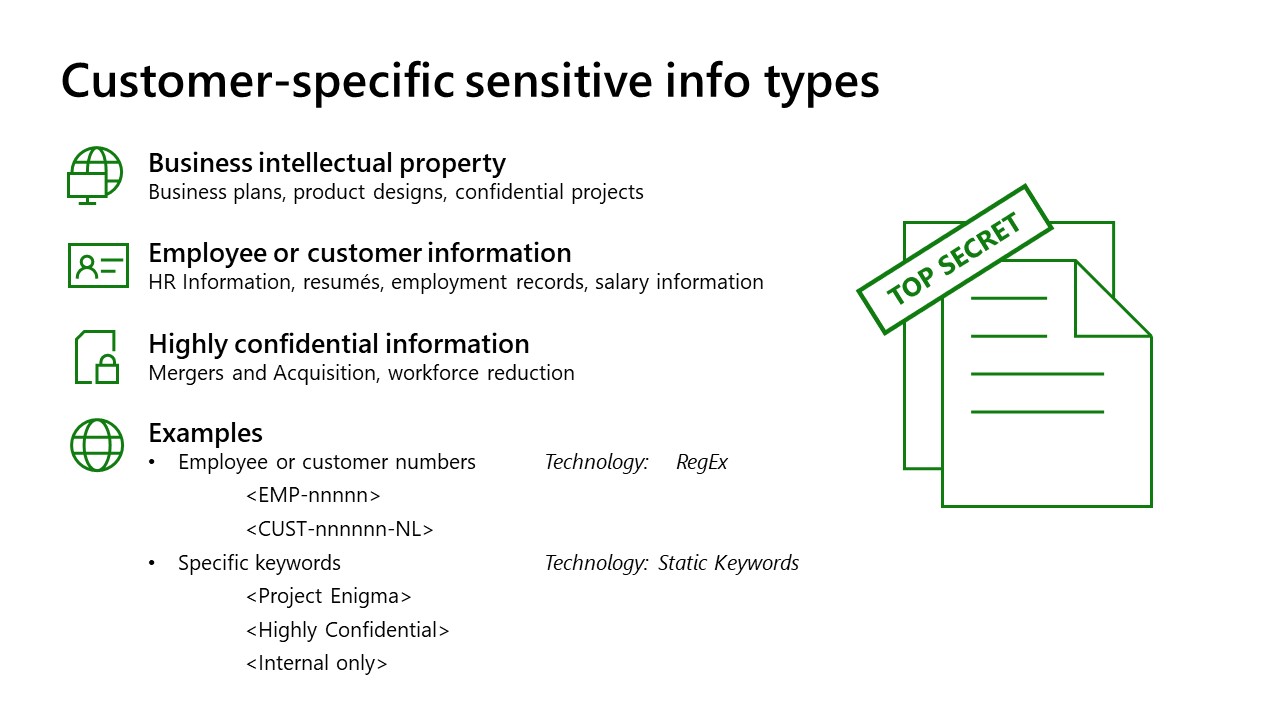
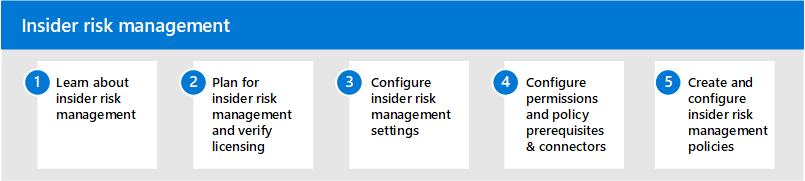
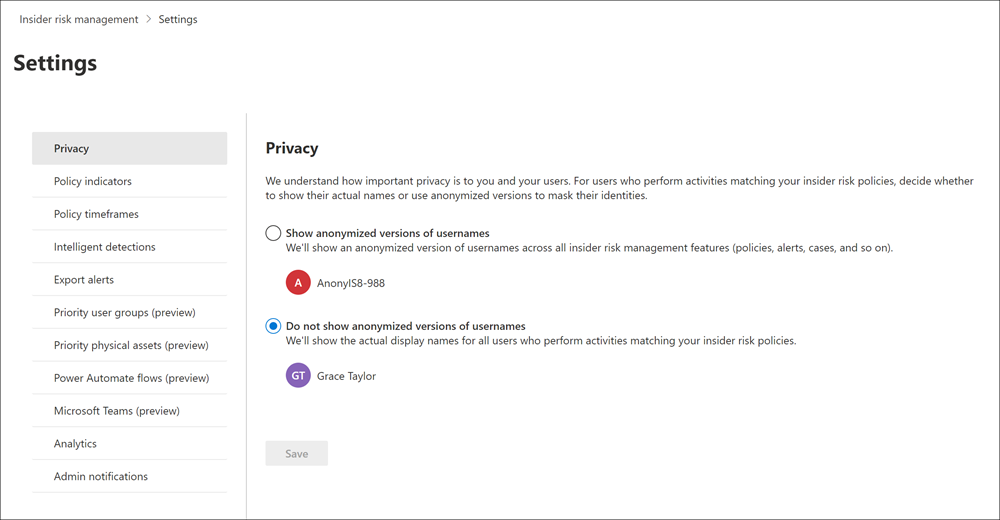
Insider Risk Management
Insider Risk Management as viewed through Microsoft Purview Compliance portal has two subsections:
Insider Risk Management
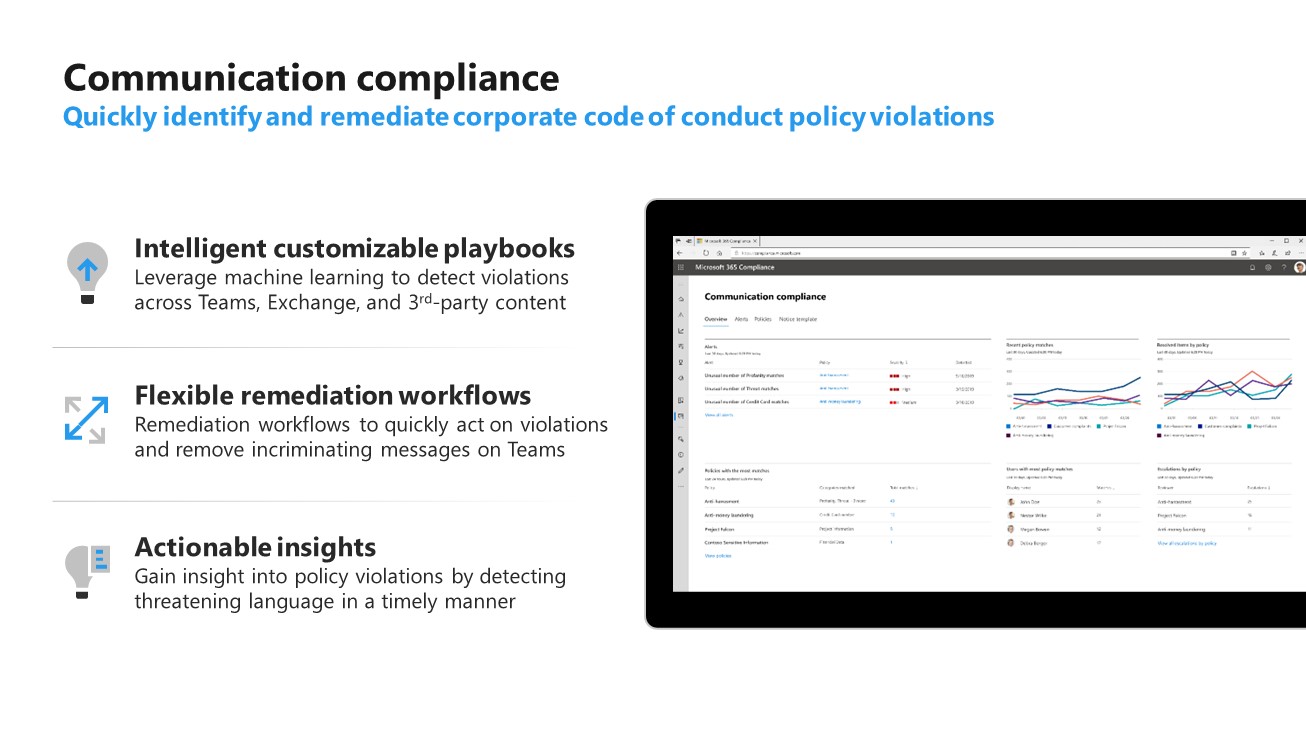
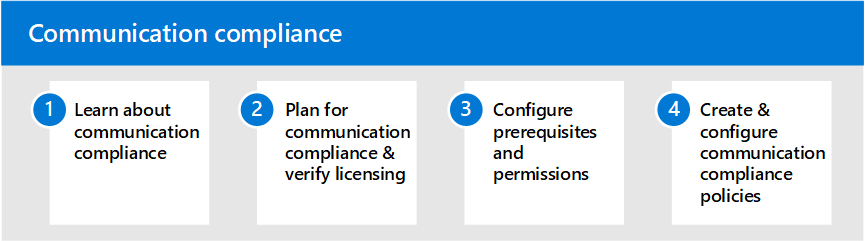
Communication Compliance
Insider Risk Management
Insider Risk Management as viewed through Microsoft Purview Compliance portal has two subsections:
Insider Risk Management


Communication Compliance


